Time for a break from the AppLocker case study to blog about this issue, since I found it very interesting.
This issue was actually discovered by me and a customer of mine by coincidence.
The issue has been run through Microsoft Security Response Center (MSRC) and they concluded that this can be fixed with a Group Policy setting. This blogpost will show the bypass and the setting you need to apply to prevent this Safe link bypass, but first I need to give a brief explanation of the safe link feature for those that are not familiar with it.
Safe links in Office 365 is a part of the Office 365 Advanced Threat Protection. If you have Office 365 Enterprise E5 or Education E5 you have this included. Office 365 Advanced Threat Protection is an add-on to Exchange online. After you buy this add-on you will get the following features:
More information on the different licenses can be found here:
https://technet.microsoft.com/en-us/library/exchange-online-advanced-threat-protection-service-description.aspx
Safe links put simple is basically a service that changes every incoming link to point to safelinks.protection.outlook.com before the mail is delivered to the users inbox. A link to google.com would look like this when it is delivered to the end user:
On the server side you can configure rules for things that should happen if a user clicks on a link that is malicious. You can read more about the different configuration options here:
https://support.office.com/en-us/article/Set-up-Office-365-ATP-safe-links-policies-bdd5372d-775e-4442-9c1b-609627b94b5d
Put simple, you choose if the safe link feature is on/off, and if the user should be allowed to visit sites that are flagged as malicious or not. You can also choose if it is supposed to be enabled for all domains or just certain users.
Here is a screenshot from the end user where the allow to visit the malicious site is enabled:

The bypass
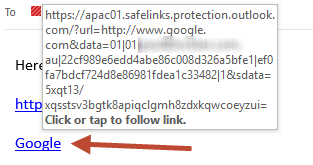
The bypass is really simple and I was surprised that this worked at all. This bypass only works if the receiver is using Outlook (AFAIK). What you do to bypass Safe link is simply to send an email to someone containing an evil link without the link. In the following screenshot you will see two different links within an email message that is about to be sent, the first will be bypassed and the second will be picked up by safe links.
Mail sent:
Mail received:
A typical example where you would use this technique is during a phishing attack.
How to protect
The easy way around this is of course to only allow plain-text mail.
The problem with that is that the users will probably complain when they have to copy every link manually instead of clicking it.
Instead I would recommend to turn of automatic conversion of text to hyperlinks in Outlook using Group Policy. The setting is named “Internet and network paths into hyperlinks” and is located directly under “User Configuration –> Administrative templates –> Microsoft Outlook 2016 –> Outlook Options”. The setting needs to be set to disabled.
After you have rolled this setting out Outlook will no turn plaintext urls into hyperlinks.
If my blogpost triggered your interest in bypassing safe links I would also recommend to check out these blogposts:
https://emtunc.org/blog/03/2017/bypassing-safe-links-exchange-online-advanced-threat-protection/
https://www.trustedsec.com/2017/02/office-365-advanced-threat-protection-features-shortfalls/
https://halon.io/blog/fooled-microsofts-safe-link-technology/
Cheers!
Timeline
- 11/11/2017 – First reported
- 13/11/2017 – MSRC created case
- 16/11/2017 – I requested an update
- 17/11/2017 – I requested an update
- 18/11/2017 – MSRC says a duplicate case exists
- 29/12/2017 – Case closed with this explaination:
“The engineering team has determined that the behavior described in that and this case is by-design – there’s not much that Safelinks can do currently against a client-side setting to autoformat plaintext into clickable hyperlinks. We are, however, evaluating the potential of adding a new feature to integrate with the Safelinks API in Outlook to address issues like this. Customers who are concerned about this issue today can push a GPO update to set the autoformat hyperlinks option as disabled.” - 03/01/2018 – Published this blogpost



I got this answer from an ATP Program Manager regarding the same thing:
Thanks for sending your email and the details of the issue. The Outlook client has a setting which makes text that looks like URLs clickable ON by default. While this is great for productivity, we believe it’s not ideal for implementing the highest level of security. For admins, they can create a GPO to change the setting and turn this setting OFF. If they’re not using Outlook, then we recommend them to switch to using Outlook for the best experience. In the future, we’ll have even tighter integrations with Outlook to cover this type of scenario even when the setting is ON. I hope that clarifies the concern.
LikeLike
Okay. Thanks for the feedback. 😊
LikeLike
Safelinks are really problematic anyways. There are a couple of ways to byepass them and they even introduce new security issues. Read: https://www.avanan.com/resources/microsoft-atp-safe-links
LikeLike
There’s another way to bypass a safelink protected in an income mail.
1) you copy the link (right click in the mail) and past it in a text editor
2) you remove the starting https://eur02.safelinks.protection.outlook.com/?url= from the copied link
3) you decode url the result -> easy with https://www.urldecoder.org/
4) comparing with the original link displayed in the income mail when you put the mouse over the link, you remove the exceeding part of the decoded url
And the resulting url works fine
LikeLiked by 1 person