I wanted to try and see if I was able to use AppLocker to only allow needed files (Real whitelisting). Normally what you would do when setting up AppLocker is that you would start out by trusting something. This something could either be everything under C:\windows and c:\programfiles, or it could be every file that is signed by Microsoft.
In this blogpost I will go over how I logged AppLocker and tried to figure out what files that is actually needed and only allow that as a base for an AppLocker policy. I ended up doing several audits and in the end I was not successful. But if someone can learn from my failures that’s great.
My Approach
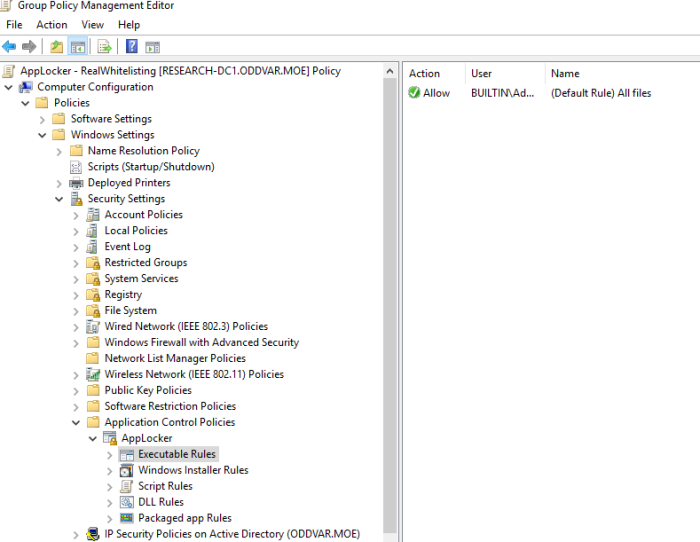
The first thing I did was to create the following path rules (Builtin\Administrators – All files) under the AppLocker configuration and I set everything up to audit:
I needed these rules or else AppLocker would not do anything. I first tried with an empty ruleset, but that did not work out.
After the first boot with the AppLocker policy active and after I logon as a normal user I generated an AppLocker policy from the audit events using these cmdlets:
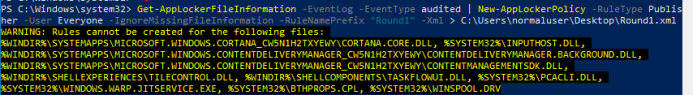
Get-AppLockerFileInformation -EventLog -EventType audited | New-AppLockerPolicy -RuleType publisher -rulenameprefix “Round1” -IgnoreMissingFileInformation -Xml > Round1.xml
There was a couple of files it could not create rules for. I did not care for those at that moment, since I knew I had to do this in several rounds. These files are highlighted in yellow in this screenshot:
These files showed in the screenshot could not become a publisher rule, meaning that they are most likely not signed correctly or missing.
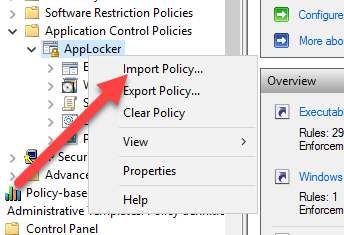
After the rules was created I then imported them to my AppLocker policy. You do that in the Group Policy editor by right clicking on the AppLocker part and selecting import.
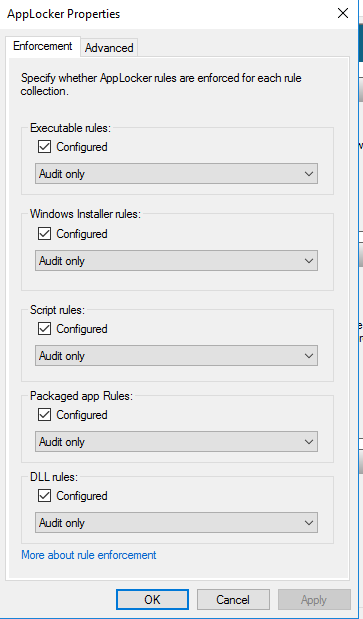
After I imported the rules I noticed that the rules apply for a specific version of the different files. I wanted to change that so that I did not have to remake this policy every time there is a new version or build. I did this by manually editing the XML file. Replacing LowSection=”versionnumber” with LowSection=”*” (and the same for HighSection). After I was done editing it I re-imported it to the AppLocker Group policy object and added rules to the different sections allowing administrators to run everything (every rule is wiped when you import). I also changed the enforcement to “Enforce rules” in each section.
Before I started round 2 I cleared the event log on the client. I did that with this Powershell line:
get-eventlog -logname * | foreach{clear-eventlog -logname $_.log}
Round 2 ended up in me not being able to logon. The vm locked up and no matter what I tried it would not boot up. Therefore I reset the vm and started over. This time with another round of auditing.
Between each round I combined the results from the event viewer into a new AppLocker policy combining the previous one with the new one. I did that with the following commands:
Get-AppLockerFileInformation -EventLog -EventType audited | New-AppLockerPolicy -RuleType publisher -rulenameprefix "Round2" -IgnoreMissingFileInformation -Xml > Round2.xml
(I did some editing in the Round2.xml, remove versions numbers etc)
Set-AppLockerPolicy -XmlPolicy C:\folder\Round1.xml (sets the local AppLocker policy on the computer to the rules defined in Round1.xml)
Set-AppLockerPolicy -XmlPolicy C:\folder\Round2.xml -Merge (Merges the Round2.xml into the local AppLocker policy that is present (Round1.xml))
I then started up gpedit.msc on the local computer I did this on and navigated to the Application Control Policy and exported the rules. These rules was then named Round2-merged.xml.
I then repeated this 7 times and I also added some rules manually as hash rules since they where missing signature.
After the 7 round I tried to set the policy to enforce and the vm’s locked up again. I then tried to only do auditing on the DLL rules and the rest to enforce, and that worked.
After some troubleshooting I gave this project up. Maybe I will continue this at some point, but to me it seems pretty hard to do true/real whitelisting with AppLocker.
I also find it strange that AppLocker rules can actually lock the boot of Windows 10. In my head the AppLocker rules are meant for the user space, not the system space.
If someone finds this deeply interesting I have exported my final ruleset and placed it here for your viewing pleasure. Note, this will probably lock your VM/Computer so do not use this in production. This is just a result of my failure.